Unlock Cloud Computing For Registered Training Organisations in Queensland
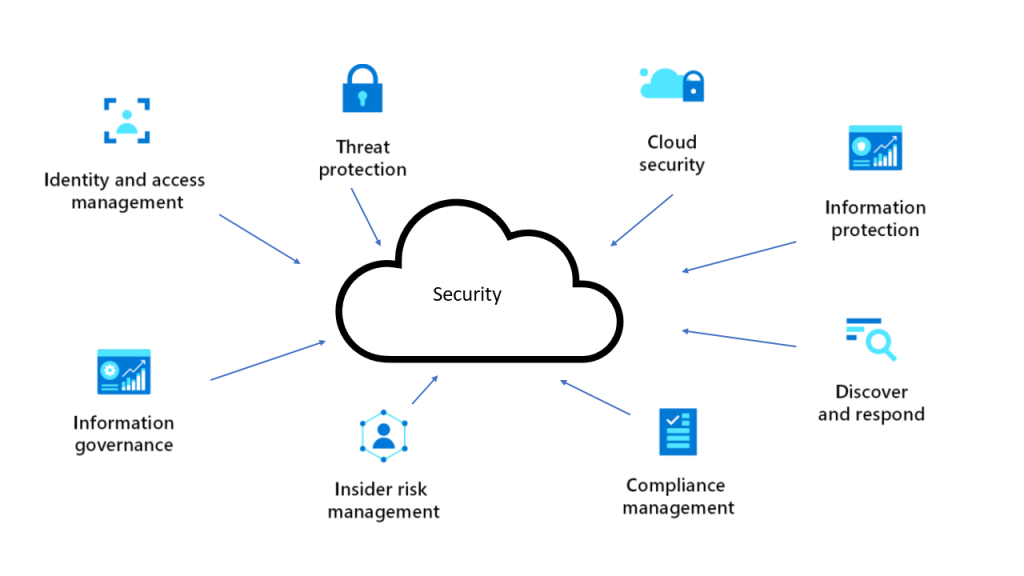
In 2025 the accelaration towards cloud computing is becoming a tsunami. It is just common sense given the savings in IT and server infrastructure organisations across Australia are moving their operations to the cloud. Businesses like Arming The Nation, a Registered Training Organisation use Cloud Services. Why Australia’s Registered Training Organisations Use Microsoft Cloud Computing […]
Unlock Cloud Computing For Registered Training Organisations in Queensland Read More »